Toolbox for VulnDetect
-
@OLLI_S Free IcoFx is vulnerable. Any suggestion in order to be able to help Tom with icons ? :-)
-
@GregAlexandre
VulnDetect detects both NirSoft IconsExtract and IcoFX.
Remember, it is only the older (portable) versions of IcoFX that are vulnerable, if you install the latest, then there is no issues.
If you find another tool, then let me know and we will add detection for that. -
@Tom I removed free and portable IcoFx as it is vulnerable.
Next time I will use NirSoft IconsExtract even if I do not like using unsupported / inactive oldies project as no one but hackers know their security status.
Regards. -
@GregAlexandre :
To extract icons I now use Quick Any2Ico : https://www.carifred.com/quick_any2ico/
Regards. -
@OLLI_S : It seems that you did not updated the site with your latest toolbox?
Still in beta?
Will you sign your .exe ? -
@GregAlexandre said in Toolbox for VulnDetect:
@OLLI_S : It seems that you did not updated the site with your latest toolbox?
Still in beta?
Will you sign your .exe ?It is still in Beta because I need to implement some features (smaller changes).
And I am waiting for a new version of Quick Any2Ico that detects the original size of the icon in the EXE file (contacted the developer but no reply yet).
I have no idea what is needed to sign an application (stopped programming 10 years ago and started it again for the Toolbox).
-
@OLLI_S ; May I suggest that you release your version even if not perfect.
Agile way of life. :)
You have to get a valid pair of key to sign code*. Then you use the private key to sign your code. The way you do it is depending of you compiler. I know to do it for macros. And more than 10 years ago I knew how to do it with Visual Studio (was it Studio ?). Quite sure you will find this very quickly in help of your compiler.- you can get needed keys at Cacert if you are assured by some assurers. Only recognize if you trust Cacert root but free and better than nothing.
-
@OLLI_S Just wanted to officially inform about some upcoming and breaking changes to the agent.
Well, breaking for the Toolbox, but not for anything else, as far as we can tell.
With the upcoming major release of the agent, it will no longer be possible to run the
--immediatein the same as way as before.The reason is simple: It doesn't make sense, because the inspection data returned by the agent are wrong, because the agent runs in the wrong context.
Instead, the
--immediatewill be changed to send a request for a new inspection task to the backend. Within 1 minute, the agent (the service) should pick up the task and inspect.This also means that the following options will be removed from the agent:
--no-filesystem --no-registry --no-system --no-msi --no-winupdate --ignore --pathThe "ignore" and "path" can still be controlled via the registry:
https://vulndetect.org/topic/2388/I don't know how many users use the Toolbox, we use it, because it is a nice way to extract data for new detections, which in turn is posted to some internal sub-categories for documentation purposes.
But the functionality to inspect is not used by anyone at SecTeer.
-
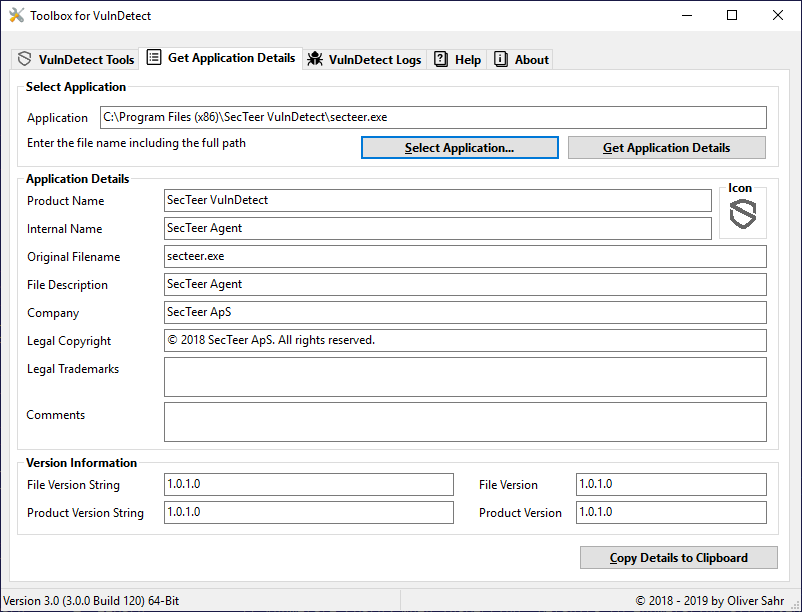
@Tom :
I use it to get apps details.
I use the beta version to get icon
In my family some were preferring the toolbox instead of the inspect button.
:-)
Greg. -
@GregAlexandre Interesting.
Luckily, I discussed this with a developer earlier today, and it seems that we can keep the
--immediatethough technically it will work quite differently.Instead of running an inspection, it will signal the service and ask it to run the inspection.
Only caveat is that it most likely will require Admin privileges to send this signal.
And then the process will exit immediately, while the service runs in the background.
The other options will still vanish because they will be incompatible with the new changes.
-
@Tom : Thanks.
But I explained that the "inspect" button now does the same thing. So no worry, for us, if the --immediate disappear.
We used the toolbox to send you a new app. :-)
Regards. -
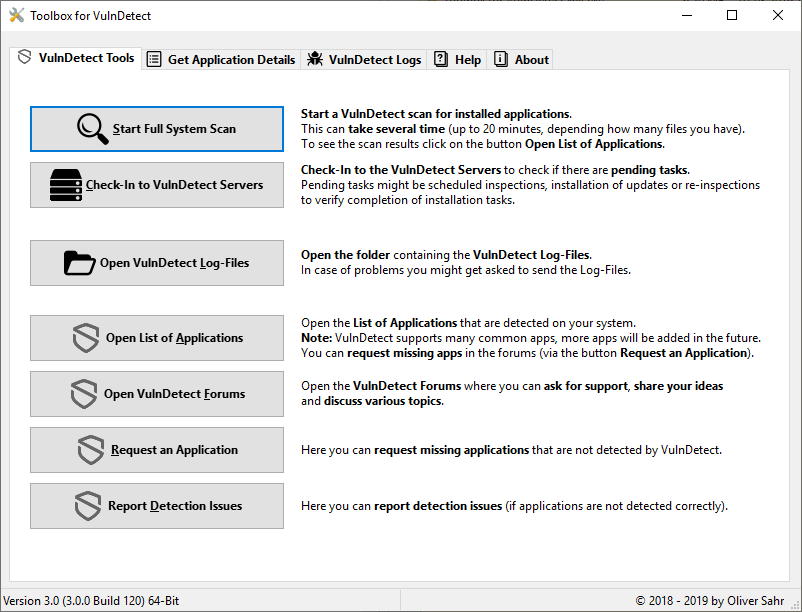
I thought about the Future of the Toolbox.
Maybe I remove the buttons Start Full System Scan and also Check-In to VulnDetect Servers.
Or maybe I remove the complete first page in the Toolbox.The next issue is the Ignored Paths.
Currently there is no UI where users can see the ignored paths and edit them.
See [Work in progress] Exclude specific drives/folders from scanIn that topic a guy called @Tom wrote at 31 Jan 2019, 17:57:
And in the long run, this will be done via the UI. Only technically savvy users should play with this in the registry or on the command line.
Hey, that was 3 Years, 9 Months and 12 Days ago.
And we still have no UI, where users can enter the ignored paths.
I think it does not make any sense to code this in the Toolbox, right?So, what is your feedback @Tom and @GregAlexandre
You both seem to be the only active users (together with me) of the toolbox.@Tom I have a new idea:
What about a web-dialog, where users drag an exe file to and the dialog performs the same things, as the toolbox (extracts the version info and also the icon)? -
-
@OLLI_S Lots of good ideas.
The first one, that about excluding drives or folders, is getting a lot closer. I don't have a date yet, but we will soon make the final decision about how it should be implemented in the backend and then it shouldn't be long before there will be a UI component for it too. -
 O OLLI_S referenced this topic on
O OLLI_S referenced this topic on
-
 O OLLI_S referenced this topic on
O OLLI_S referenced this topic on